 Jimmy, on 16 April 2014 - 08:47 PM, said:
Jimmy, on 16 April 2014 - 08:47 PM, said:
I believe Nacho also has this. He had to have gotten the screenshots on the DNF 2D Wikia page somewhere.
I'll add one:
 Jimmy, on 16 April 2014 - 08:47 PM, said:
Jimmy, on 16 April 2014 - 08:47 PM, said:
 Jimmy, on 16 April 2014 - 07:24 PM, said:
Jimmy, on 16 April 2014 - 07:24 PM, said:
 Frederik Schreiber, on 16 April 2014 - 10:27 PM, said:
Frederik Schreiber, on 16 April 2014 - 10:27 PM, said:
This post has been edited by StrikerMan780: 17 April 2014 - 12:27 AM
 StrikerMan780, on 17 April 2014 - 12:24 AM, said:
StrikerMan780, on 17 April 2014 - 12:24 AM, said:
Quote

This post has been edited by Hendricks266: 26 August 2021 - 02:20 PM
Reason for edit: revived image





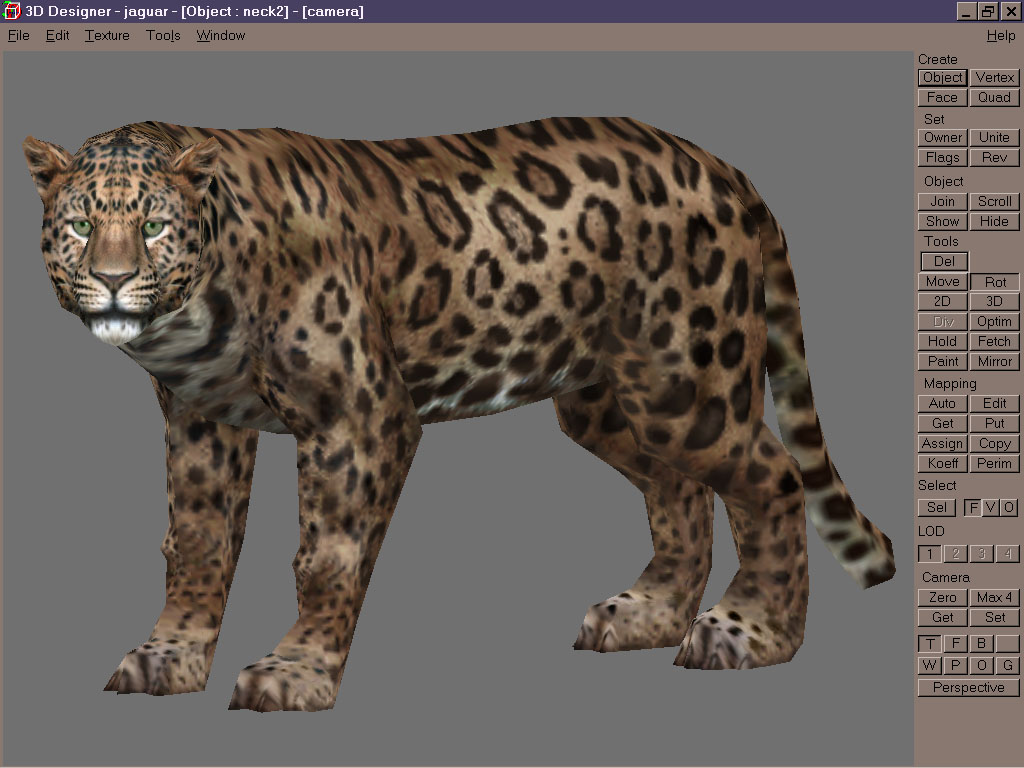
This post has been edited by Hendricks266: 14 January 2023 - 08:39 PM
Reason for edit: revived images
 Lunick, on 17 April 2014 - 04:58 AM, said:
Lunick, on 17 April 2014 - 04:58 AM, said:
This post has been edited by Frederik Schreiber: 17 April 2014 - 05:01 AM
This post has been edited by Daedolon: 17 April 2014 - 05:31 AM
This post has been edited by TheZombieKiller: 17 April 2014 - 05:40 AM
 Jimmy, on 16 April 2014 - 08:47 PM, said:
Jimmy, on 16 April 2014 - 08:47 PM, said:
This post has been edited by Hendricks266: 14 January 2023 - 09:01 PM
Reason for edit: revived image
 Frederik Schreiber, on 17 April 2014 - 09:35 AM, said:
Frederik Schreiber, on 17 April 2014 - 09:35 AM, said:
/* Directory of C:\DEV\SW\MIDI EXECUT11 MID HROSHMA6 MID HOSHIA02 MID INTRO131 MID KOTEC2 MID KOTOKI12 MID NIPPON34 MID NOKI41 MID SANAI MID SIANRA23 MID TKYO2007 MID TYTAIK16 MID YOKOHA03 MID */
 angelo86, on 17 April 2014 - 09:47 AM, said:
angelo86, on 17 April 2014 - 09:47 AM, said:
 Frederik Schreiber, on 17 April 2014 - 09:49 AM, said:
Frederik Schreiber, on 17 April 2014 - 09:49 AM, said: